Process Library
iaai currently use 6 Master Categories:
CATEGORY 1 — Financial Services & Banking Workflows
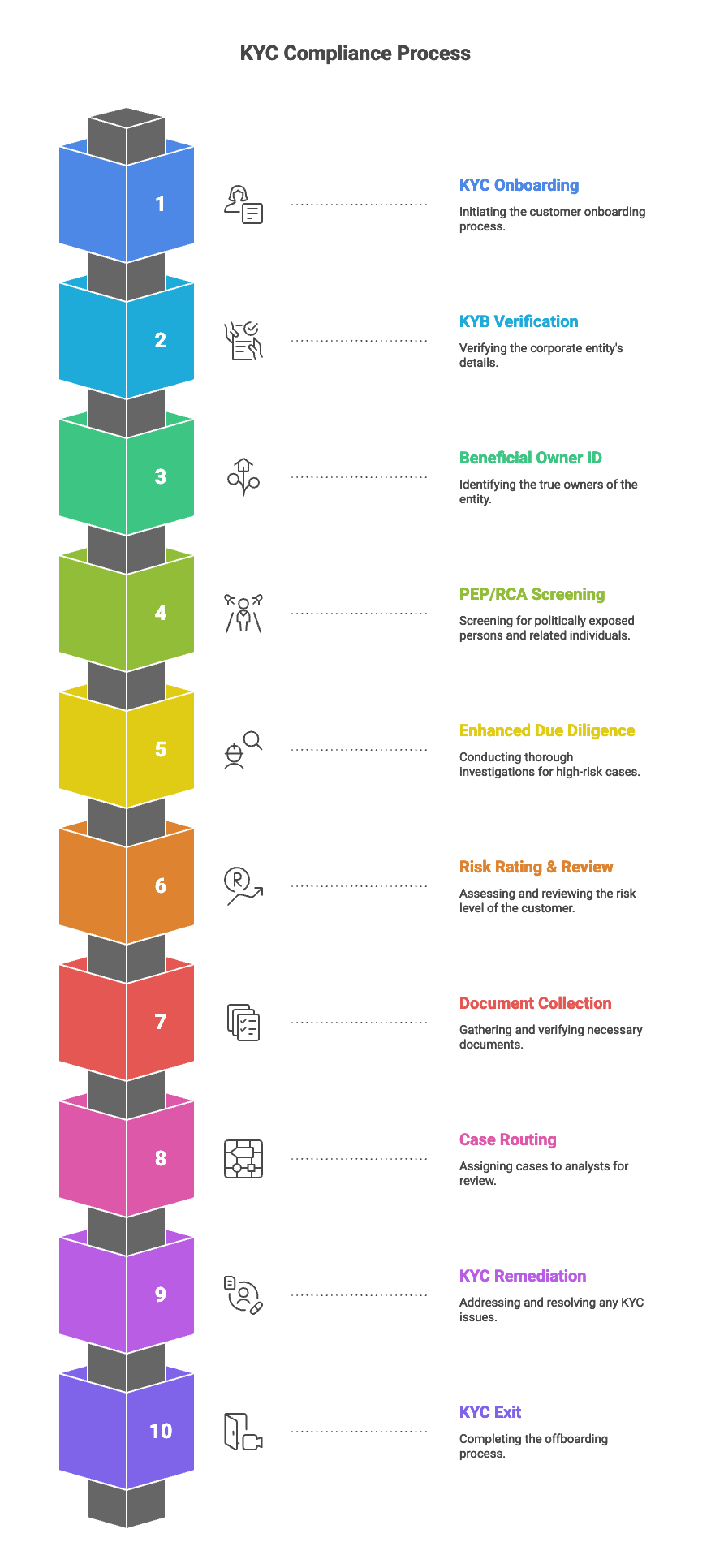
1. KYC / KYB Onboarding
KYC Initial Customer Onboarding Flow
KYB Corporate Entity Verification Flow
Beneficial Owner Identification
PEP / RCA Screening & Approval
Enhanced Due Diligence (EDD)
Risk Rating & Periodic Review Cycle
Document Collection & Verification
Case Routing & Analyst Assignment
KYC Remediation Cycle
KYC Exit & Offboarding Workflow
2. AML Investigations
Transaction Monitoring Alert Handling
Level 1 → Level 3 AML Escalation
AML Investigation Case Structure
Evidence Collection & Audit Trail
SAR Preparation & Filing
Post-SAR Customer Treatment
AML Quality Assurance Workflow
AML Model Governance Cycle
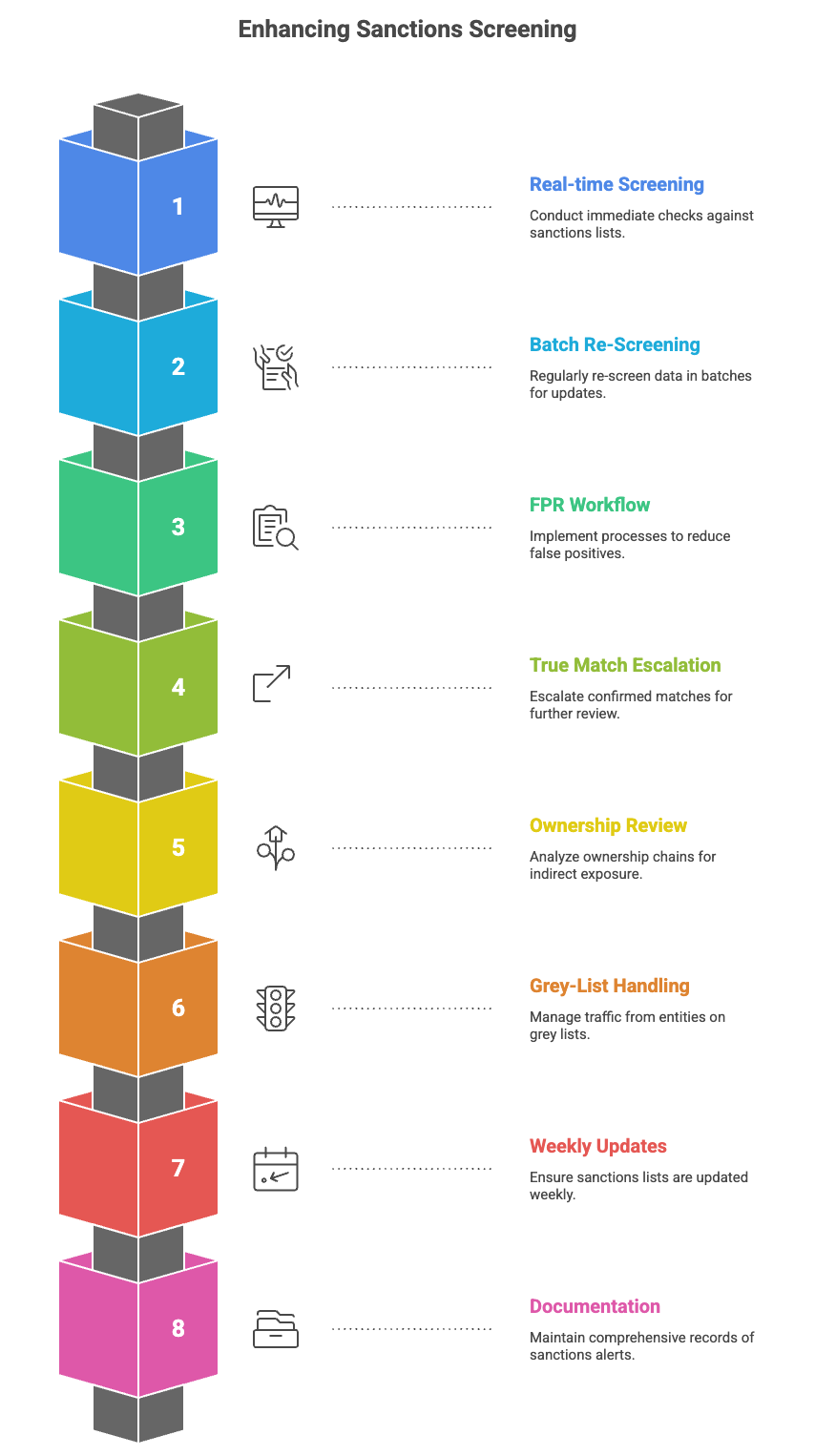
3. Sanctions & Screening
Real-time Sanctions Screening Flow
Batch Re-Screening Process
False Positive Reduction (FPR) Workflow
True Match Escalation (Level 2 Review)
Indirect Exposure / Ownership Chain Review
Grey-List Traffic Handling
Weekly List Updates Workflow
Sanctions Alert Documentation Requirements
4. Fraud Detection & Risk Operations
Fraud Alert → Triage → Case Workflow
Behavioural Analytics Exception Handling
Chargeback Handling Flow
Identity Fraud (IDV Failure) Handling
Account Takeover Workflow
Card Not Present Fraud Investigation
Internal Fraud Escalation Pathway
5. Credit & Underwriting
Credit Application Processing
Risk Decisioning Logic
Manual Underwriting Flow
Document Collection & Verification
Appeal & Exception Handling
Credit Limit Review Cycle
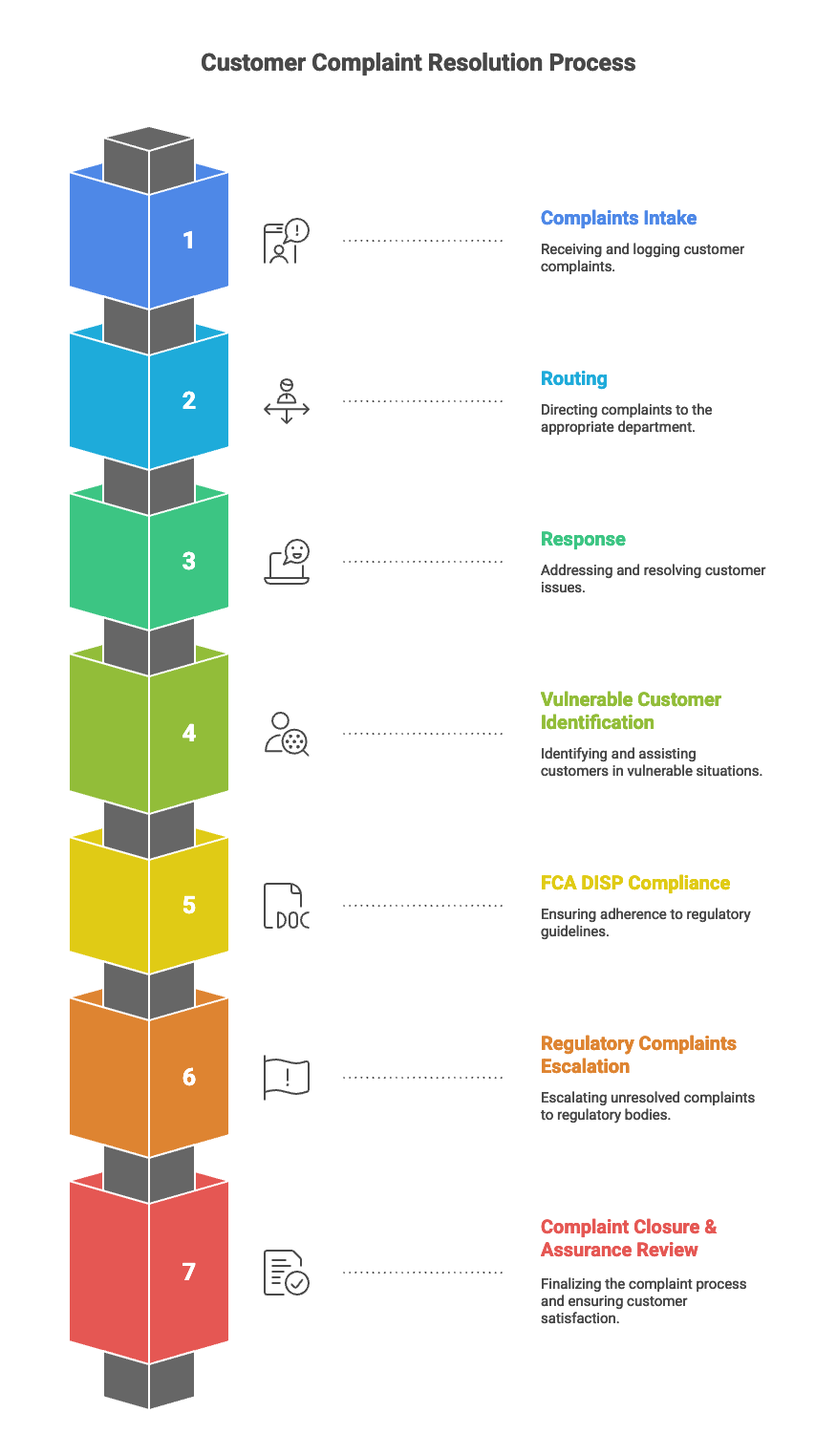
6. Customer Operations & Complaints
Complaints Intake → Routing → Response
Vulnerable Customer Identification Flow
FCA DISP Compliance Workflow
Regulatory Complaints Escalation
Complaint Closure & Assurance Review
CATEGORY 2 — Regulated Gambling Workflows
1. Player Onboarding & Verification
IDV → AML → KYC Flow
SOF (Source of Funds) Verification
SOW (Source of Wealth) Review
Player Risk Rating Assignment
Data Enrichment Workflow
Failed Verification → Next Steps
2. Safer Gambling Workflows
Marker of Harm Detection
Automated Behavioural Flagging
Manual Review Flow
Player Conversations & Interventions
Temporary Restrictions Workflow
Permanent Exclusion Workflow
Regulatory Reporting & Evidence Capture
3. AML (Gambling-Specific)
AML Alert Handling
Transaction Pattern Analysis
AML Case Documentation
Interaction Requirements
High-Risk Customer Controls
Reporting to Regulator
4. Fraud & Risk
Bonus Abuse Workflow
Multi-Accounting Detection
Device & IP Risk Scoring
Payment Fraud → Triage → Case
Suspicious Activity Escalation
🟣 5. VIP & High-Value Players
VIP Eligibility Assessment
Enhanced Due Diligence (EDD)
Responsible Gambling Monitoring
Ongoing Compliance Review
CATEGORY 3 — Law Firm Workflows
1. Matter Intake
New Client Check
Conflict Check
AML / CDD for Clients & Parties
Engagement Letter Workflow
Matter Setup in PMS
Fee Structure Approvals
Matter Acceptance Governance
2. Ongoing Legal Operations
Document Lifecycle Workflow
Data Protection Workflow
GDPR/PII Handling
DLP (Data Loss Prevention) Approval Path
Secure File Transfer & Review
3. Risk & Compliance
High-Risk Matter Escalation
Sanctions Checks for Legal Clients
Politically Exposed Client Assessment
Ethical Wall Setup
Breach Reporting Workflow
⚖️ 4. Billing & Financial
Timekeeping → Pre-Bill → Billing Cycle
Audit Trail for Adjustments
Credit Control Workflow
CATEGORY 4 — Energy & Utilities Workflows
1. Field Operations
Maintenance Request Workflow
Permit to Work
Site Safety Checklists
Field Incident Escalation
Equipment Failure Investigation
2. Regulatory & Compliance
Environmental Incident Reporting
Audit Preparation Cycle
Risk Assessment & Mitigation
ESG Reporting Workflow
3. Supplier & Contractor Management
Supplier Onboarding
Supplier Risk Assessments
Contract Compliance Review
CATEGORY 5 — Cross-Industry Automation Workflows
1. AI-Powered Document Automation
Document Intake → Classification → Extraction
Accessibility Remediation Workflow
Privacy & Security Scanning
Tagging → Structuring → QA
Exception Handling
Human-in-the-loop Approval
2. RPA Automation
Trigger → Bot Execution → Audit Logging
Error Handling Workflow
BOT QA & Release Management
CATEGORY 6 — Governance, Controls & Operating Models
1. Control Frameworks
1st/2nd/3rd Line Workflow
QA → QC → Audit Trail
Evidence Pipeline
Risk Scoring Engine Flow
2. Operating Model Design
RACI → Process → Controls Mapping
Policy to Procedure Flow
Governance Oversight Cycle
PHASE 2 — BEGINNING THE DETAILED LIBRARY CONTENT
PROCESS 1: KYC Onboarding Workflow (Full Detail)
Purpose
To onboard individual customers while meeting regulatory, risk, and compliance expectations for identity verification and financial crime controls.
Primary Stakeholders
KYC Analyst
Compliance
Operations
Risk
Relationship Manager
Automation Systems
Screening Vendors
High-Level Stages
Customer Application Intake
Identity Verification (IDV)
Sanctions / PEP Screening
Risk scoring
Document Collection
Enhanced Due Diligence (if triggered)
Approval / Decline
Customer Activation
Audit & Evidence Logging
Detailed Stage Breakdown
1. Application Intake
Customer submits application through onboarding flow
Personal information captured
System triggers IDV provider (OCR, biometric, validation checks)
Failure logic: Retry → Manual Review → Reject
2. Identity Verification
ID document authenticity checks
Liveness detection
Face match algorithms
Additional triggers: mismatched data → manual check
3. Screening
Real-time screening for:
PEP
RCA
Sanctions lists
False positive reduction
Hit categorisation (Level 1, Level 2)
4. Risk Scoring
Automated risk score based on:
Geography
Occupation
Behaviour models
Device intelligence
Customer profile
5. Document Collection
Request bank statements / proof of address / financial documents
Automation extracts key fields
Exceptions routed to analysts
6. Enhanced Due Diligence
Triggers include:
High-risk country
Adverse media
Wealth inconsistency
Sanctions match
EDD steps:
Deeper document checks
Source of wealth review
Senior Management escalation
7. Approval / Decline
All steps logged
Evidence files packaged
Compliance sign-off
8. Activation
Customer record created
Access enabled
Ongoing monitoring triggers registered
9. Audit Trail
Full documentation
Screening snapshot
Analyst notes
EDD evidence archive
Policy references
Financial Services & Banking — KYC / KYB Onboarding
Full Lifecycle Processes
Purpose: Verify identity, assess financial crime risk, and produce a fully auditable onboarding record.
Includes:
– Application Intake
– IDV (document, biometric, liveness)
– Sanctions / PEP / RCA Screening
– Adverse Media Review
– Risk Scoring
– Document Collection
– EDD Where Required
– Case Routing
– Compliance Approval & Activation
Purpose: Confirm the legitimacy of business clients and establish beneficial ownership.
Includes:
– Corporate Registry Verification
– Active Status Check
– BO Mapping
– UBO Identity Checks
– PEP/RCA Screening
– Industry Risk Scoring
– Offshore / Shell EDD
– MLRO Approval
Mapping natural persons with direct/indirect control over legal entities using FATF, FCA, and EU AMLD6 definitions.
Includes:
– Ownership hierarchy analysis
– Control-based BO assessment
– >25% and >10% thresholds
– Screening of directors & UBOs
– MLRO escalation for complex cases
Real-time screening for politically exposed persons, their relatives, and close associates.
Includes:
– Hit identification
– False positive reduction rules
– Level 1/2 review
– Enhanced monitoring setup
– Compliance approval documentation
Deep due diligence procedures for high-risk individuals and entities.
Includes:
– Source of Wealth validation
– Adverse media deep-dive
– Jurisdictional analysis
– High-risk industry checks
– Senior approval workflow
– EDD evidence file
Application of customer risk scoring and assignment of review cadence.
Includes:
– Transaction profile analysis
– AML behaviour risk mapping
– Periodic review rules
– Triggered review (sanctions, adverse media)
Verification of identity, address, financial documents, corporate filings, and risk evidence.
Includes:
– OCR extraction
– Metadata validation
– Fraud detection flags
– Cross-registry verification
– Analyst evidence notes
– Compliance sign-off
Automated or manual assignment based on risk, complexity, and SLA requirements.
Routing:
– Low → Automated
– Medium → Analyst
– High → Senior Analyst
– PEP/Sanctions → Compliance
– Complex KYB → Specialist Team
Triggered updates due to expired documents, risk changes, or regulatory updates.
Includes:
– Outreach
– Doc refresh
– Re-screening
– Re-assessment
– Compliance review
– Evidence archive
Formal removal of customers who fail to meet compliance requirements.
Includes:
– Account freeze
– AML investigation
– SAR filing (if required)
– Customer notification
– Archive evidence
– Do-Not-Onboard flag
Services KYC / AML / Sanctions • Automation & RPA • Process Engineering • Regulatory Alignment • Governance & Controls • Operational Model Redesign
Sectors Financial Services • Banking • Global Law Firms • Regulated Gambling • Energy & Utilities • Enterprise & Public Sector
Resources Process Library • Case Studies • Compliance Frameworks • Insights & Research Company About • Leadership • Careers • Contact • Security & Trust Center
Legal Privacy Policy • Terms of Service • Accessibility • Data Processing Agreement
Copyright © 2025 iaai.
All rights reserved. Operates globally under applicable regulatory and data protection frameworks..
At iaai, our mission is simple: to make AI more personal, accessible, and meaningful. Let’s transform the way you complete tasks